Introduction
In the constantly evolving realm of cybersecurity, tools that can effectively identify and mitigate vulnerabilities are invaluable. One such tool, standing out in its utility and accessibility, is Zed Attack Proxy (ZAP). This open-source security tool, often simply known as ZAP, has become a cornerstone in the toolkit of security professionals and enthusiasts alike.
Origins of ZAP
ZAP was created by Simon Bennetts, a renowned figure in the cybersecurity community, as part of the Open Web Application Security Project (OWASP). It was first released in 2010 and has since been developed and maintained by a global community of volunteers. The genesis of ZAP lies in the need for an easy-to-use tool for finding vulnerabilities in web applications, which was accessible even to those who were not security experts.
Why ZAP?
The benefits of using ZAP in cybersecurity are manifold:
- Open Source and Community-Driven: Being an OWASP project, ZAP is free and open-source, allowing for constant improvements and updates from a worldwide community of developers.
- User-Friendly Interface: ZAP is designed to be user-friendly, making it accessible for both beginners and experienced professionals. Its intuitive GUI facilitates easy navigation and operation.
- Comprehensive Testing: ZAP offers a range of automated scanners as well as tools for manual penetration testing, making it a comprehensive solution for web application testing.
- Active and Passive Scanning: ZAP provides both active scanning, which sends malicious requests to the server, and passive scanning, which inspects the application’s responses without sending harmful requests.
- Extensibility and Customization: Users can extend and customize ZAP according to their needs through a wide range of plug-ins.
- Community and Documentation: ZAP benefits from a robust community and extensive documentation, making troubleshooting and learning more accessible.
- Integration with Other Tools: ZAP can be integrated with other tools in the security domain, enhancing its capabilities and allowing for a more thorough security analysis.
As we dive into the practical applications of Zed Attack Proxy (ZAP), our focus will shift to a hands-on exploration of vulnerabilities within a controlled environment. For this purpose, we will utilize Metasploitable2, an intentionally vulnerable virtual machine widely used for training and educational purposes in the field of cybersecurity. Specifically, our attention will be centred on the ‘Mutillidae’ section of Metasploitable2.
Mutillidae, a part of the Metasploitable2 suite, is an intentionally vulnerable web application that provides a real-world environment for testing and understanding web application vulnerabilities. It is a perfect candidate for our demonstration due to its designed vulnerability, making it an ideal learning platform for penetration testing techniques.
In this practical guide, we will walk through the process of scanning Mutillidae using ZAP. Our goal is to uncover the potential vulnerabilities that reside within this application. This exercise is not just about finding weaknesses but also about understanding the nature of these vulnerabilities. By doing so, we aim to gain a deeper insight into how such vulnerabilities can be exploited and, more importantly, how they can be mitigated in real-world scenarios.
This hands-on approach will serve as an invaluable learning experience, demonstrating the effectiveness of ZAP in identifying vulnerabilities in web applications. Whether you are a beginner in the field of cybersecurity or a seasoned professional, this exploration will provide you with practical knowledge and skills that are essential in the ever-evolving landscape of web security. So, let’s gear up and dive into the world of web application vulnerabilities with ZAP and Metasploitable2’s Mutillidae!
Automated Scanning with ZAP on Metasploitable2’s Mutillidae
In our journey to uncover vulnerabilities within the Mutillidae application on Metasploitable2, we will utilize ZAP’s powerful automated scanning feature. Our target for this exercise will be a specific URL: http://10.10.1.105/mutillidae/index.php?page=user-info.php. This approach allows us to focus our testing on a particular aspect of Mutillidae, providing a more detailed and in-depth analysis of potential vulnerabilities.
Initiating the Automated Scan
Upon targeting this URL, we will initiate an automated scan using ZAP. This process involves two crucial stages: Spidering and Active Scanning.
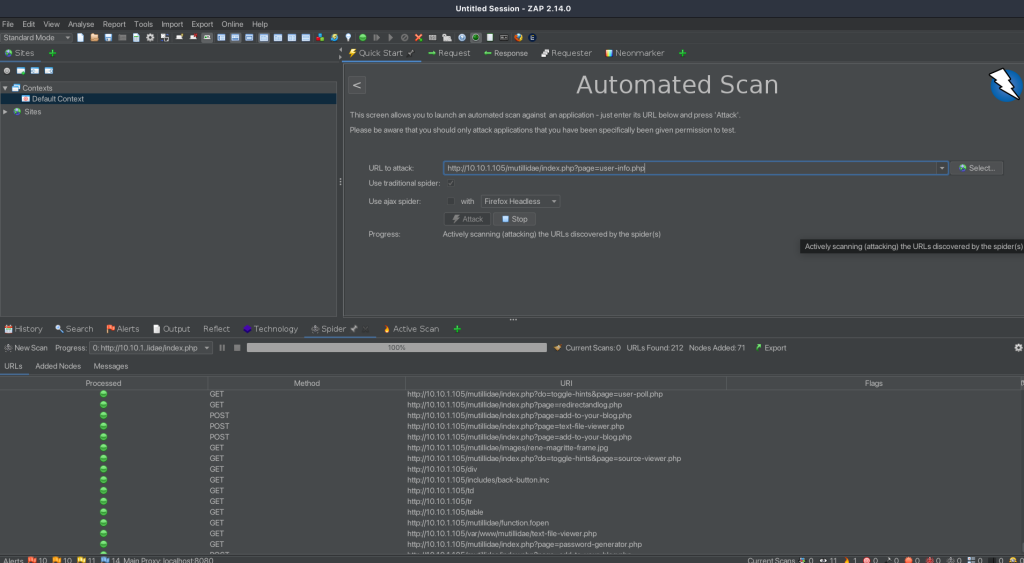
Spidering: Mapping the Web Application
The first stage in our automated scan is ‘Spidering’. Here’s what happens during this phase:
- Exploration: The spider tool in ZAP crawls through the targeted web application, much like a search engine spider. It systematically browses the site, following links, and exploring content.
- Mapping: As it crawls, the spider is building a map of the application structure, including directories, pages, and different elements like forms and inputs.
- Discovery: This process helps in discovering hidden and visible content that might not be immediately apparent. It is crucial for understanding the full scope of the application.
The spidering stage is essential as it lays the groundwork for a comprehensive scan. It ensures that the subsequent active scanning phase covers as much of the application as possible.
Active Scanning: Searching for Vulnerabilities
Following the spidering phase, we proceed to ‘Active Scanning’, which is more aggressive and direct in identifying vulnerabilities:
- Probing: Active scanning involves sending various inputs and requests to the application. These are designed to probe for common vulnerabilities like SQL injection, cross-site scripting, and others.
- Analysis: ZAP analyses the responses from these probes to identify patterns or behaviours indicating a vulnerability.
- Reporting: Each potential vulnerability is logged, and detailed information about the nature of the issue, including risk level and possible mitigation strategies, is provided.
Active scanning is a critical phase where actual vulnerabilities are identified. It’s a more intrusive method compared to spidering and is designed to simulate real-world attacks on the application.
The Synergy of Spidering and Active Scanning
By combining spidering and active scanning, ZAP ensures a thorough examination of the web application. Spidering ensures that the active scan covers a broad area of the application, while active scanning delves deep into these areas to uncover potential security issues.
As we embark on this automated scanning process, we anticipate uncovering a range of vulnerabilities within the Mutillidae application. This exercise will not only highlight the strengths of ZAP as a security tool but also provide practical insights into the nature and identification of common web application vulnerabilities.
Detailed Overview of Automated Active Scanning in ZAP
In our endeavour to analyse the vulnerabilities of the Mutillidae application on Metasploitable2, we have engaged ZAP’s automated active scanning feature. This comprehensive and robust tool goes through an extensive list of tests to uncover potential security issues. Below is a detailed overview of the active scanning process we conducted, showcasing the breadth and depth of ZAP’s capabilities in identifying vulnerabilities.
Active Scanning Process
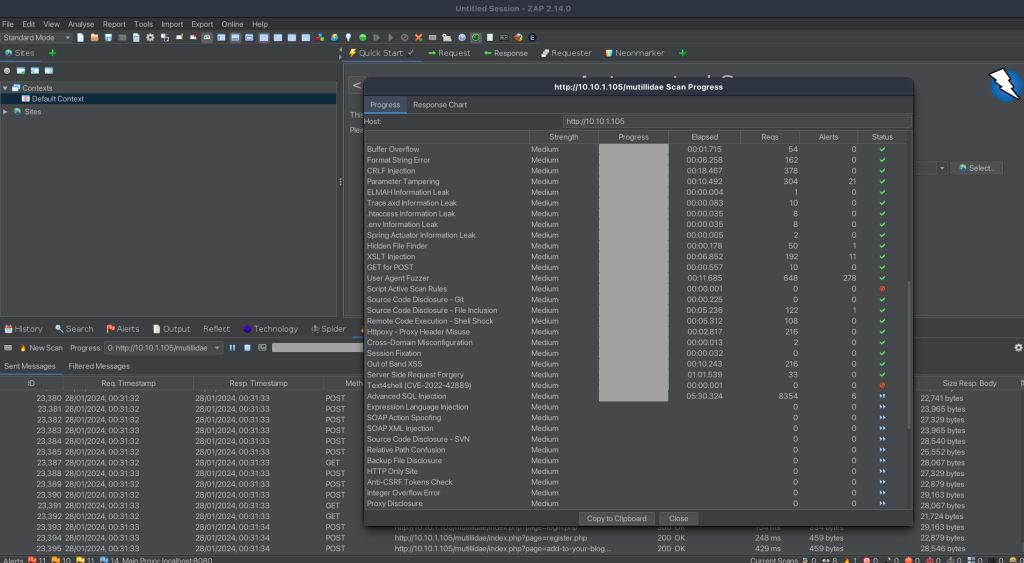
The active scanning involved a variety of tests, each targeting different types of vulnerabilities. Here’s a breakdown of what each test entailed and the results it yielded:
- Path Traversal: Tested for vulnerabilities that allow access to files and directories stored outside the web root folder. Detected 18 alerts.
- Remote File Inclusion: Checked for the ability to include remote files through the web application. Found 1 alert.
- Heartbleed OpenSSL Vulnerability: Searched for the Heartbleed vulnerability, a security bug in the OpenSSL cryptography library. No alerts were found.
- Source Code Disclosure: Tested for multiple types of source code disclosure vulnerabilities, including those in the /WEB-INF folder and CVE-2012-1823 vulnerabilities. Detected a total of 18 alerts.
- Remote Code Execution: Checked for remote code execution vulnerabilities, particularly the CVE-2012-1823 vulnerability. Found 18 alerts.
- Cross-Site Scripting (XSS): Conducted tests for both reflected and persistent XSS vulnerabilities, resulting in 30 alerts for reflected XSS.
- SQL Injection: Tested for various types of SQL injection vulnerabilities across different databases, including MySQL, PostgreSQL, and SQLite. Detected 10 alerts in general SQL Injection and 10 more in SQLite Injection.
- Server Side Template Injection: Checked for template injection vulnerabilities, both regular and blind, but found no alerts.
- Directory Browsing: Tested for the ability to list directories on the server. Found 6 alerts.
- Buffer Overflow and Format String Error: Checked for vulnerabilities that could allow buffer overflow attacks and format string errors, but no alerts were found.
- Parameter Tampering: Tested for vulnerabilities that could arise from tampering with URL parameters. Detected 21 alerts.
- XSLT Injection: Checked for vulnerabilities in XSLT processing. Found 11 alerts.
- User Agent Fuzzer: Tested how the application responds to various user-agent strings. Found 278 alerts.
- Server Side Request Forgery (SSRF): Checked for vulnerabilities that could allow an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker’s choosing. No alerts were found.
- Advanced SQL Injection: Conducted a more in-depth search for SQL injection vulnerabilities, finding 9 alerts.
- NoSQL Injection – MongoDB: Tested for NoSQL injection vulnerabilities specific to MongoDB. Detected 1 alert and was still running at the time of reporting.
- LDAP Injection: Checked for vulnerabilities that could allow LDAP injection attacks. No alerts were found.
- Cookie Slack Detector: Tested for issues related to cookie handling. Found 51 alerts.
- Insecure HTTP Methods: Checked for HTTP methods that could be insecurely used. Found 28 alerts.
- Other Tests: Included checks for issues like CORS headers, HTTP parameter pollution, insecure content delivery, and more. Various alerts were found across these tests.
Total Results
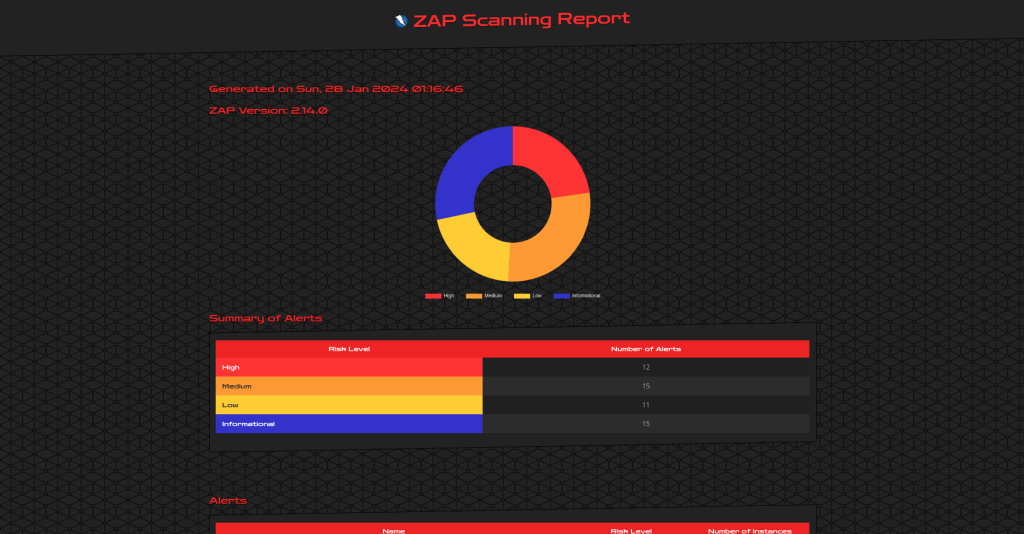
The active scan ran for a total of approximately 18 hours and 18 minutes, processing 29,563 requests and identifying a total of 545 alerts. This extensive testing showcases ZAP’s ability to conduct a deep and thorough analysis of web applications for a wide array of vulnerabilities.
The results from this scan provide invaluable insights into the security posture of the Mutillidae application. Each identified vulnerability represents a potential security risk that needs to be addressed to ensure the application’s safety and integrity. The active scan performed by ZAP serves as an effective tool for cybersecurity professionals to identify and mitigate these risks.
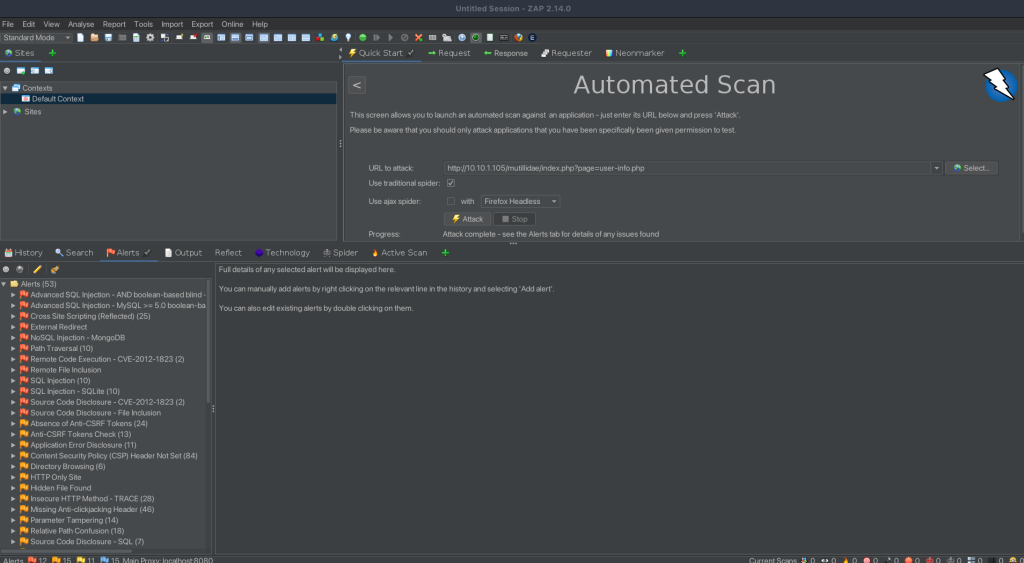
Understanding the Alerts and Findings from ZAP Scanning
After running an extensive automated scan on the Mutillidae application using ZAP, we have a comprehensive list of alerts that highlight potential vulnerabilities. These alerts range from common web application vulnerabilities like SQL Injection and Cross-Site Scripting (XSS) to more specific issues like Path Traversal and LDAP Injection. The results, with a total of 545 alerts, provide a broad overview of the security landscape of the application.
The Nature of Automated Scanning Alerts
It’s crucial to understand the nature of these alerts:
- Severity Levels: Alerts vary in severity from informational to critical. It’s important to prioritize the handling of these alerts based on their potential impact.
- Description and Details: Each alert includes a description and often suggestions for remediation. This information is vital for understanding the nature of the vulnerability and how it can be mitigated.
- False Positives: Automated scans, while efficient, are not foolproof. They can sometimes generate false positives, indicating a vulnerability where none exists.
The Importance of Manual Verification
Given the possibility of false positives, manual verification becomes a critical step in the vulnerability assessment process. Here’s why manual testing is essential:
- Accuracy: Manual testing allows for a more accurate assessment of each identified vulnerability. It helps confirm whether an alert is a true positive or a false positive.
- Context Understanding: Automated tools lack the context that human judgment provides. Manual testing helps understand the context of the application, its functionality, and how a vulnerability can practically impact it.
- Complex Vulnerabilities: Some vulnerabilities, especially those that involve complex logic or specific application contexts, may only be identifiable or confirmable through manual testing.
- Customized Attacks: Automated scans follow a predefined set of rules and patterns. Manual testing allows for customized attack scenarios that are more aligned with the specific architecture and logic of the application.
Combining Automated and Manual Approaches
The ideal approach to security testing involves a blend of both automated and manual testing. While automated scans with tools like ZAP provide a broad overview and identify obvious vulnerabilities efficiently, manual testing allows for a deeper dive into specific areas, especially where the automated scans indicate potential issues. This combination ensures a more comprehensive and accurate vulnerability assessment.
In summary, the results from our ZAP scan on Mutillidae are a starting point. They provide valuable insights but should not be taken at face value without manual verification. This two-pronged approach of using automated tools supplemented by manual testing forms the backbone of a robust and effective web application security assessment strategy.
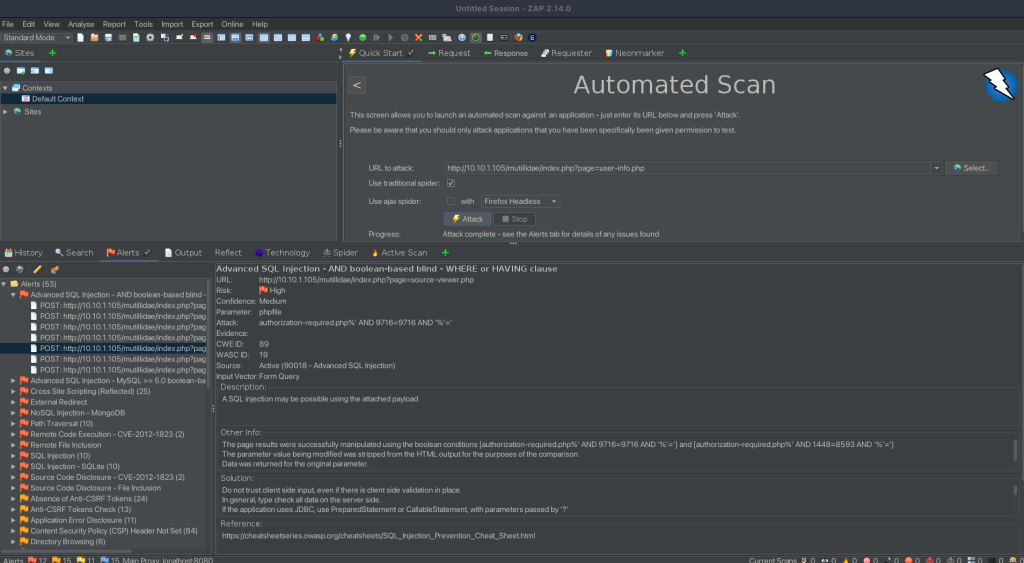
Analysis of the Advanced SQL Injection Alert in ZAP
The Nature of the Attack
The first alert we are analysing is an “Advanced SQL Injection – AND boolean-based blind – WHERE or HAVING clause.” This type of attack is a sophisticated form of SQL Injection, where the attacker attempts to extract data from a database by sending SQL queries that the database executes. The “boolean-based blind” technique involves sending queries that return a different result based on a condition being true or false, even when no direct data is returned. The attacker infers data based on these true/false conditions.
Evidence Found
The evidence of this vulnerability was discovered upon inputting the URL http://10.10.1.105/mutillidae/index.php?page=source-viewer.php. This action allowed us to view the source code of the show-log.php file. The source code revealed several indicators of vulnerability:
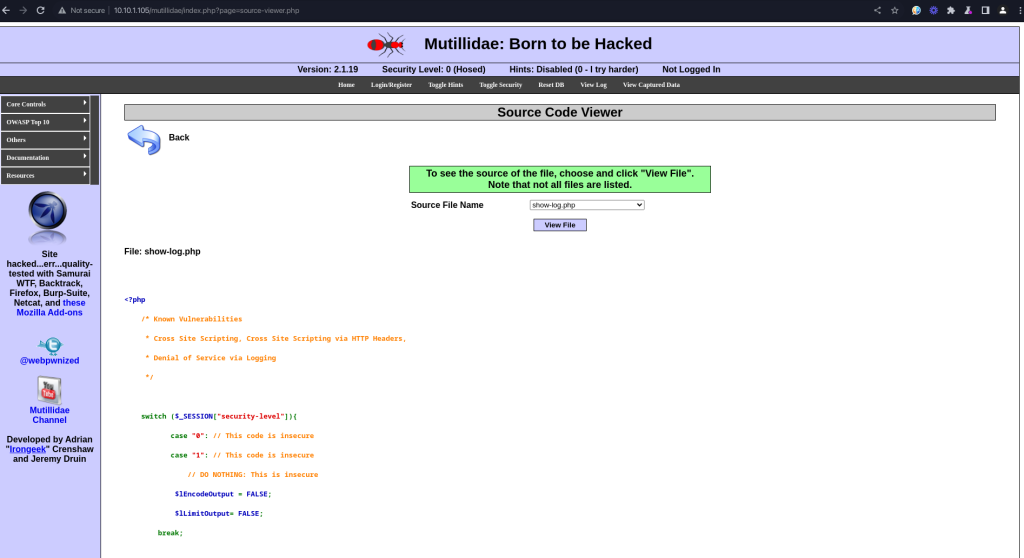
- Lack of Input Validation: The code switches security levels but does not consistently validate or sanitize the input, particularly at lower security levels.
- Potential Query Manipulation: The application constructs SQL queries using parameters obtained from user input (
$_GETand$_SESSIONvariables), which can be manipulated. - Conditional Responses: The code logic suggests that the application’s response may vary based on the input, which is a typical condition for boolean-based SQL injection.
The Danger of This Vulnerability
The danger posed by this type of vulnerability is significant:
- Data Breach: Attackers can extract sensitive data from the database, including personal information, credentials, and other confidential data.
- Unauthorized Access: It can lead to unauthorized access to other parts of the application or system, depending on the nature of the data obtained.
- Potential for Further Attacks: Knowledge gained from successful SQL injections can be used to craft more targeted attacks, escalating the threat level.
- Compromise of Database Integrity: Beyond data theft, attackers can modify or delete data, compromising the integrity of the application’s database.
- Legal and Reputational Damage: Data breaches can result in legal consequences and severe damage to an organization’s reputation.
Mitigation Strategies
To mitigate this vulnerability, the following actions should be considered:
- Input Validation and Sanitization: Implement robust input validation and sanitization to ensure that only valid data is processed.
- Prepared Statements and Parameterized Queries: Use prepared statements with parameterized queries in the application to prevent SQL injection.
- Least Privilege Access: Ensure that the database user connected to the application has the least privilege necessary, limiting what an SQL injection attack can accomplish.
- Regular Code Audits and Security Testing: Regularly audit the application code for vulnerabilities and conduct thorough security testing.
- Security Training: Educate developers about secure coding practices to prevent such vulnerabilities from being introduced.
In conclusion, the discovery of this SQL injection vulnerability through ZAP’s automated scanning highlights the importance of thorough security practices in web application development and maintenance. Proper mitigation efforts are crucial to safeguard against such vulnerabilities and protect sensitive data.
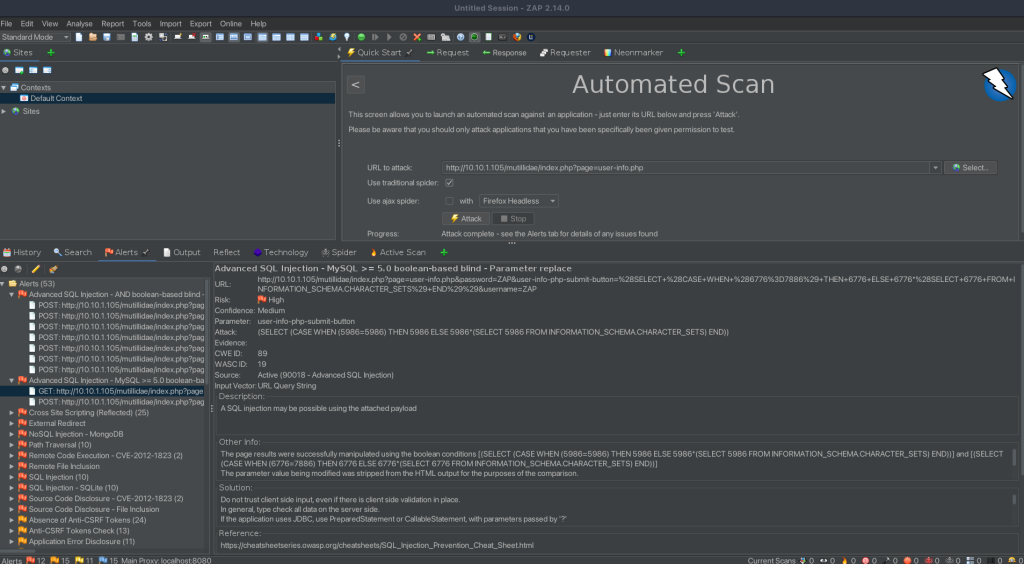
Analysis of the Advanced SQL Injection Alert: MySQL >= 5.0 Boolean-Based Blind – Parameter Replace
Overview of the Attack
The second alert we’re examining is an “Advanced SQL Injection – MySQL >= 5.0 boolean-based blind – Parameter replace.” This form of attack is a specialized SQL Injection aimed at MySQL databases version 5.0 or higher. It involves manipulating SQL queries by replacing parameters with conditional SQL statements. The “boolean-based blind” aspect implies that the attacker infers information from the database based on boolean conditions (true/false) without directly seeing the data.
Evidence Found
The vulnerability was identified using the URL: http://10.10.1.105/mutillidae/index.php?page=user-info.php&password=ZAP&user-info-php-submit-button=(SELECT (CASE WHEN (6776=7886) THEN 6776 ELSE 6776*(SELECT 6776 FROM INFORMATION_SCHEMA.CHARACTER_SETS) END))&username=ZAP.
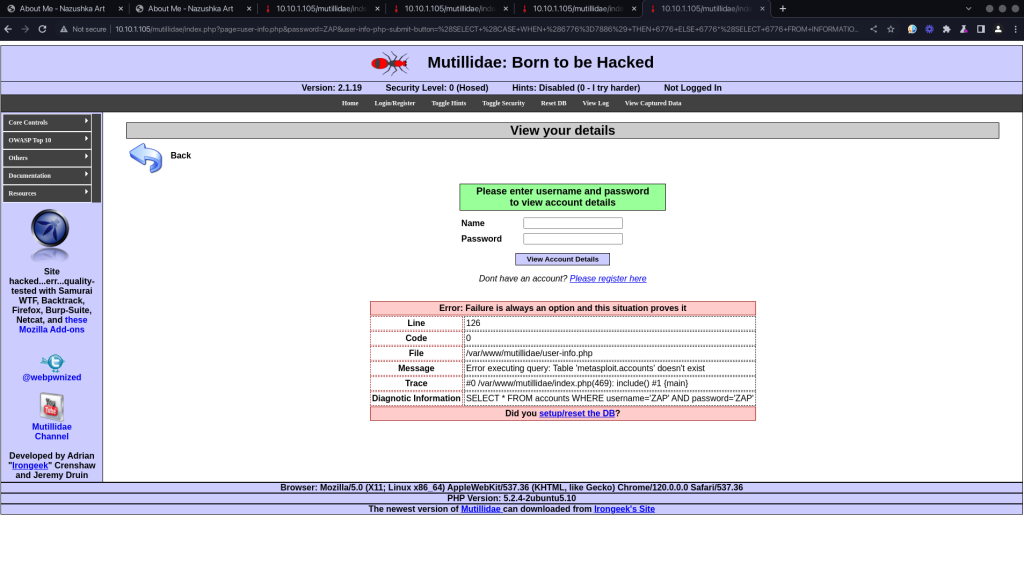
This URL includes a manipulated parameter that injects a SQL CASE statement into the application’s normal SQL query. The injected statement checks a condition (6776=7886), which is false, and then triggers an alternative action. The query attempts to multiply a number by a dataset extracted from the database’s internal INFORMATION_SCHEMA.CHARACTER_SETS table, a behaviour not intended under normal circumstances.
The Danger of This Vulnerability
The risks associated with this vulnerability include:
- Extraction of Sensitive Data: The attacker can use similar techniques to extract sensitive information from the database.
- Database Enumeration: It allows for database enumeration, where an attacker can learn about the database structure, including table names and column details.
- Database Manipulation: Beyond data theft, such vulnerabilities can allow attackers to manipulate or destroy data.
- Elevated Access: In some cases, these vulnerabilities can be exploited to escalate privileges within the application or the underlying system.
- Chain Attacks: Once an attacker understands the database structure, it can lead to more sophisticated attacks, using the gathered information.
Mitigation Strategies
To mitigate this type of SQL injection, consider the following:
- Use of Prepared Statements: Use prepared statements with parametrized queries to ensure the separation of code and data.
- Regular Expression Checks: Implement regular expression checks on input data to prevent the injection of unwanted SQL tokens.
- Error Handling: Ensure that error messages do not disclose sensitive information about the database structure.
- Web Application Firewall (WAF): Deploy a WAF that can detect and block SQL injection attempts.
- Security Audits and Updates: Regularly audit your web applications and databases for vulnerabilities and apply necessary patches and updates.
- Education and Awareness: Train developers in secure coding practices, emphasizing the importance of input validation and parameterized queries.
Conclusion
This particular instance of SQL injection demonstrates the nuanced ways in which attackers can exploit seemingly minor vulnerabilities in web applications. Understanding the mechanics of such attacks is vital for developers and security professionals to effectively safeguard against them. Proactive and comprehensive security measures are key to maintaining the integrity and safety of web applications.
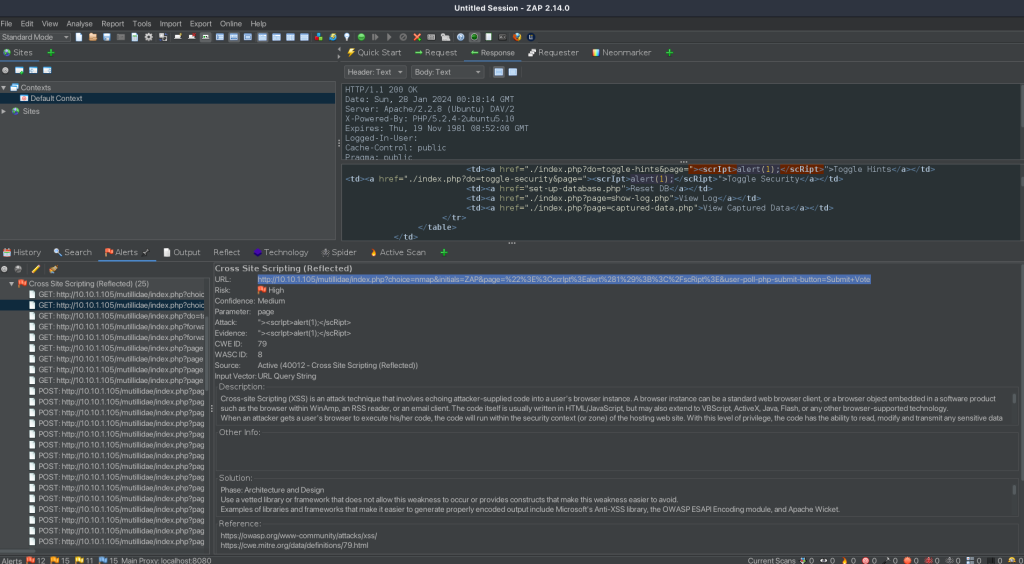
Analysis of the Cross-Site Scripting (Reflected) Alert
Understanding the Attack
The alert in question is a “Cross-Site Scripting (Reflected)” vulnerability. Reflected Cross-Site Scripting (XSS) occurs when an application receives data in a request and includes that data in the immediate response in an unsafe way. Unlike stored XSS, reflected XSS is not permanently stored on the target’s server or database; instead, the XSS script is reflected off the web server and executed directly in the victim’s browser.
Evidence Found
The vulnerability was identified through the following URL: http://10.10.1.105/mutillidae/index.php?choice=nmap&initials=ZAP&page="><scrIpt>alert(1);</scRipt>&user-poll-php-submit-button=Submit+Vote. This URL injects a script (<script>alert(1);</script>) into the application’s response.
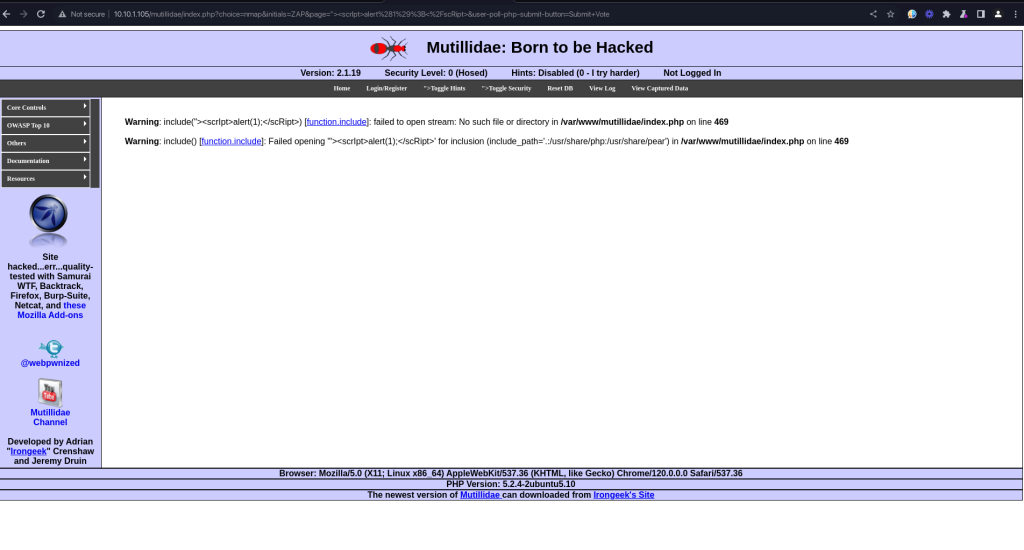
The server’s response with warnings:
Warning: include("><scrIpt>alert(1);</scRipt>) [function.include]: failed to open stream: No such file or directory in /var/www/mutillidae/index.php on line 469Warning: include() [function.include]: Failed opening '"><scrIpt>alert(1);</scRipt>' for inclusion (include_path='.:/usr/share/php:/usr/share/pear') in /var/www/mutillidae/index.php on line 469
These warnings indicate that the server attempted to process the injected script as a file path, which failed, but crucially, the script was not properly sanitized or escaped, leading to its inclusion in the response.
The Danger of This Vulnerability
The risks associated with reflected XSS include:
- Stealing Cookies: Attackers can steal session cookies, leading to session hijacking.
- Phishing: XSS can be used to create convincing phishing sites or redirect users to malicious sites.
- Executing Malicious Scripts: It allows for arbitrary execution of scripts in a user’s browser, which can lead to further exploitation.
- Bypassing CSRF Protections: XSS can be used to bypass CSRF protections, making it possible to perform actions on behalf of users.
- Damaging User Trust: Successful XSS attacks can damage the reputation of the website and erode user trust.
Mitigation Strategies
To protect against reflected XSS, consider the following measures:
- Input Sanitization: Ensure all user input is properly sanitized before being reflected back in output.
- Content Security Policy (CSP): Implement a robust CSP to prevent the execution of unauthorized scripts.
- Escaping Data: Escape all user-controlled data based on the context in which it’s displayed (HTML, JavaScript, CSS, URL, etc.).
- Regular Security Auditing: Regularly audit your website for XSS vulnerabilities and patch them promptly.
- Educating Developers: Train developers in secure coding practices, emphasizing the importance of input validation and output encoding.
Conclusion
Reflected XSS vulnerabilities like this one highlight the importance of treating all user input as potentially malicious. Implementing a multi-layered security approach that includes input validation, output encoding, and CSP can significantly reduce the risk of such vulnerabilities.
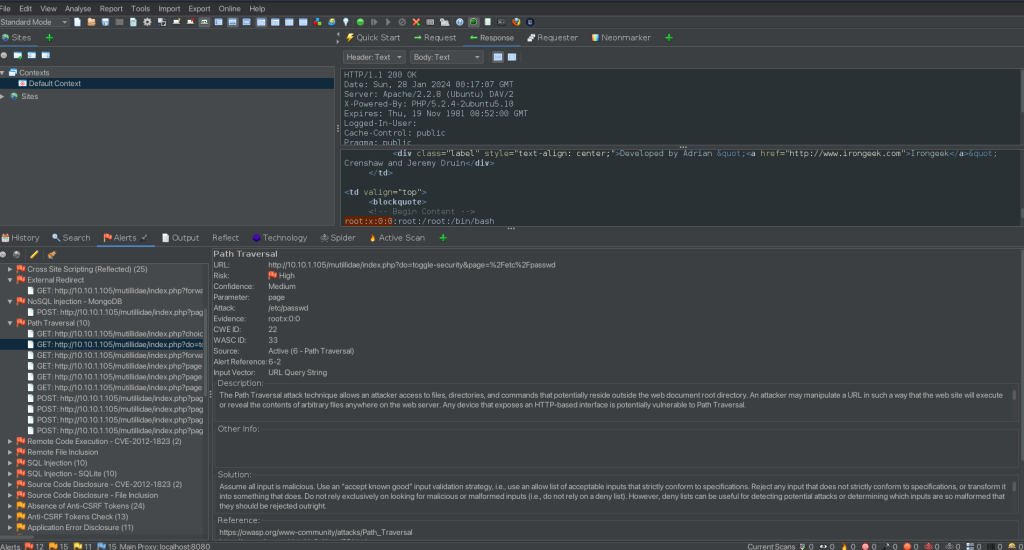
Analysis of the Path Traversal Alert
Understanding the Attack
The alert we are examining now is a “Path Traversal” vulnerability. Path Traversal, also known as Directory Traversal, is an attack which allows attackers to access files and directories that are stored outside the web application’s root directory. Attackers manipulate variables that reference files with ../ sequences and similar methods, attempting to access files and directories stored on the server file system.
Evidence Found
The vulnerability was identified through the URL: http://10.10.1.105/mutillidae/index.php?do=toggle-security&page=%2Fetc%2Fpasswd. By manipulating the page parameter in the query string, the attacker is able to traverse out of the intended directory and access the /etc/passwd file, a critical system file in Unix-like operating systems.
The server’s response included contents from the /etc/passwd file, which lists information about each user on the system. This response indicates that the application is not properly sanitizing the input to prevent directory traversal attacks, thus allowing access to files outside of the intended directories.
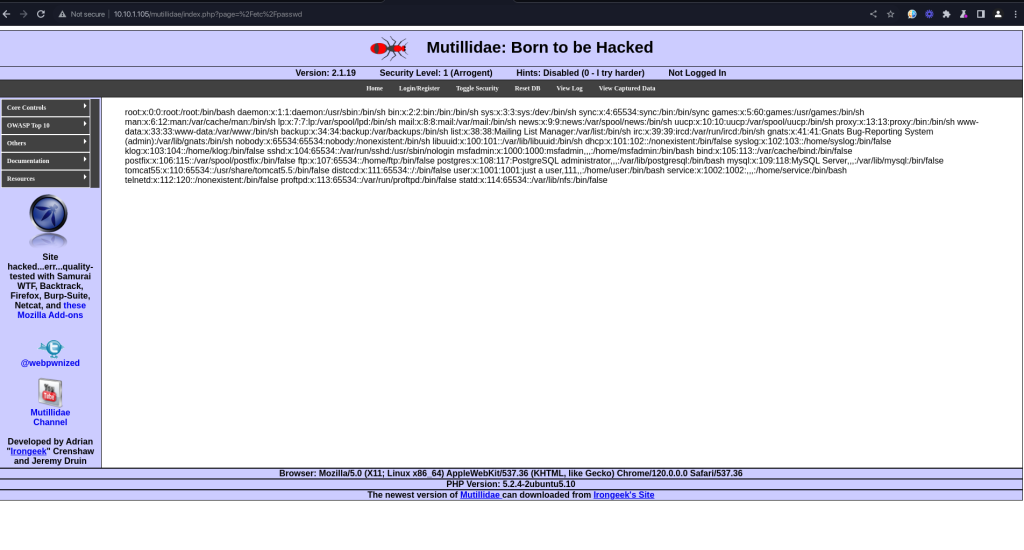
The Danger of This Vulnerability
The risks associated with Path Traversal include:
- Exposure of Sensitive Files: Files containing sensitive information, such as system files, configuration files, and data files, can be accessed and read.
- Information Leakage: The
/etc/passwdfile, for example, contains a list of users on the system, which can be valuable information for an attacker. - Potential for Further Exploitation: Accessing certain files might lead to further attacks or exploitation, especially if configuration files or scripts with exploitable content are accessed.
- System Compromise: In severe cases, if files like executable scripts or system configuration files are accessed and manipulated, it could lead to a full system compromise.
Mitigation Strategies
To protect against Path Traversal, consider the following measures:
- Input Validation: Implement strict validation of user-supplied input, rejecting any suspicious or malformed input.
- Use of Safelists: Employ a safelist of allowed files and deny access to any file not on the list.
- Limiting File Access: Ensure the web application runs with the least privileges necessary, limiting the files that can be accessed.
- Using Secure File Handling APIs: Use file handling APIs that inherently manage path traversal vulnerabilities.
- Regular Audits and Updates: Regularly audit your web applications for vulnerabilities like path traversal and keep your systems and applications updated.
Conclusion
The discovery of this Path Traversal vulnerability underscores the importance of rigorous input validation and system security measures in web application development. Preventing such vulnerabilities is crucial for protecting sensitive data and maintaining the integrity and security of the system.
The exercise of using Zed Attack Proxy (ZAP) to scan the Mutillidae application within Metasploitable2 has provided us with a valuable opportunity to understand and analyse a range of web application vulnerabilities. Through this process, we’ve uncovered and delved into various types of vulnerabilities, each highlighting critical aspects of web application security.
Key Insights
- Variety of Vulnerabilities: From SQL Injection and Cross-Site Scripting (XSS) to Path Traversal, the diversity of vulnerabilities detected underscores the multifaceted nature of web application security.
- Severity and Impact: The vulnerabilities we explored vary in their severity and potential impact. Some like SQL Injection could lead to significant data breaches, while others like XSS pose a threat to end-user security.
- Real-World Implications: Each vulnerability, while discovered in a controlled environment, represents real-world threats that exist in many web applications. These examples serve as a reminder of the potential dangers lurking in insufficiently secured applications.
- Importance of Manual Verification: The need for manual verification in conjunction with automated tools like ZAP cannot be overstated. While automated scans are efficient in identifying potential vulnerabilities, manual analysis is crucial for accurate validation and understanding the context of each finding.
- Mitigation Strategies: The identified vulnerabilities highlight the importance of implementing robust security practices such as input validation, secure coding, use of security headers, and regular security audits.
Broader Implications for Cybersecurity
- Continuous Learning and Adaptation: The field of cybersecurity is continuously evolving. Staying informed about emerging threats and vulnerabilities is crucial for security professionals and developers.
- Proactive Security Culture: These findings emphasize the need for a proactive approach to security, integrating secure practices throughout the development life-cycle.
- Community and Collaboration: Tools like ZAP, developed and maintained by the cybersecurity community, exemplify the importance of collaboration and knowledge sharing in the field.
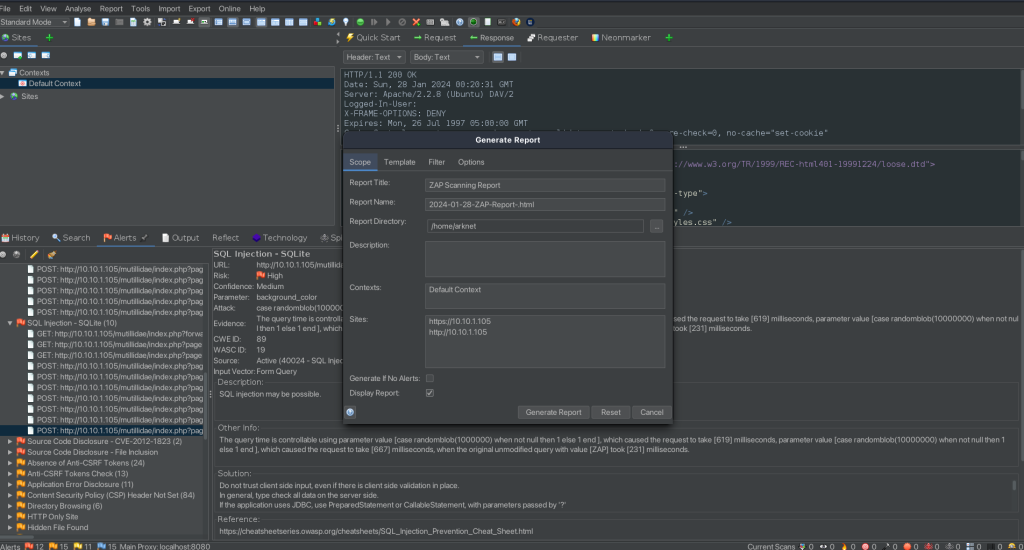
Generating an HTML Report in ZAP: A Step-by-Step Guide
Zed Attack Proxy (ZAP) provides the functionality to generate detailed reports of your findings in various formats, including HTML. An HTML report is particularly useful for presenting findings in a visually accessible manner, which can be easily shared and reviewed by team members who may not have access to ZAP. Here’s a step-by-step guide on how to generate an HTML report in ZAP:
Step 1: Complete Your Scan
Ensure that your scan is complete. ZAP can generate reports at any time, but for a comprehensive report, it’s best to do this after your scans have fully finished.
Step 2: Access the Report Generation Feature
- Open ZAP.
- Navigate to the top menu bar.
- Click on the “Report” menu option.
Step 3: Select ‘Generate HTML Report’
Under the ‘Report’ menu, you will find several options for different types of reports. Select “Generate HTML report…”. This opens a dialog box where you can configure your report.
Step 4: Configure Report Options
In the dialogue box, you can typically choose:
- The sections to include in the report (like Alerts, Passive Scan Results, etc.).
- Optionally, you can filter the alerts to include based on their Risk level or Confidence level.
Step 5: Save the Report
- After configuring the options, click “Generate” or “OK” (the exact wording may vary depending on the version of ZAP).
- You will be prompted to choose a location to save your HTML report. Navigate to the directory where you want to save the report.
- Enter a name for your report and ensure the file extension is “.html”.
- Click “Save”.
Step 6: View the Report
- Navigate to the location where you saved your report.
- Open the HTML file in any web browser to view your report.
Step 7: Review and Share
- Review the report for any critical vulnerabilities or issues that need attention.
- Share the report with your team, stakeholders, or clients as needed. Since it’s in HTML format, it can be viewed in any web browser without the need for specialized software.
Tips for Effective Reporting
- Customize Your Report: Tailor the report to your audience. For technical teams, include detailed technical information. For executive summaries, focus on high-level findings and impacts.
- Follow Up on Findings: Use the report as a basis for remediation. Assign tasks to team members for addressing identified vulnerabilities.
- Maintain Records: Keep copies of reports for future reference and to track the progress of your security posture over time.
Generating an HTML report in ZAP is a straightforward process that turns your scan results into an accessible and shareable document, aiding in the effective communication of vulnerabilities and needed actions within your organization.
Disclaimer:
The information provided in this article is for educational and informational purposes only. The tools and methods discussed are intended to be used in a legal and ethical manner. Testing web applications for vulnerabilities should only be conducted on systems for which you have explicit permission to do so. Unauthorized testing or hacking of websites or applications is illegal and unethical.
The examples and scenarios presented are based on a controlled environment with an intentionally vulnerable application (Metasploitable2’s). They are designed to educate readers about common vulnerabilities in web applications and how to detect them using tools like Zed Attack Proxy (ZAP). The vulnerabilities and methods discussed may not apply to all systems and are not a comprehensive guide to web application security.
While every effort has been made to provide accurate and up-to-date information, the rapidly evolving nature of cybersecurity means that the tools, techniques, and vulnerabilities discussed may change. Therefore, readers are advised to always ensure they are using the latest versions of any security tools and to stay informed about current best practices in cybersecurity.
This article does not constitute professional security advice, and readers are encouraged to consult with professional cybersecurity experts for specific advice and guidance. The author and publisher of this article are not responsible for any illegal or unethical actions carried out based on the information provided, nor for any damages or losses connected with the use of this information.





